VeraHunter
VeraHunter is a powerful software solution designed specifically for law enforcement agencies to identify VeraCrypt containers. It acts as helping hand for GovCracker, our decryption software.


VeraHunter – a VeraCrypt container detection software
VeraHunter is a powerful and free software solution designed to identify VeraCrypt containers and thus make important information accessible in the context of criminal investigations. It acts as helping hand for GovCracker, our decryption software and provides additional helper functions. Both tools have been designed to support law enforcement agencies, universities, IT forensic based organizations and lawyers.
Click on the next link, if you want to jump to VeraHunters download section. If you just want to get a brief introduction of the software itself, you could take a look at our screenshot examples, or at our – soon to follow – videos.
How does VeraHunter work?
In the modern era of the internet, cybercrimes are occuring on a daily basis. This poses significant challenges for IT forensics-oriented organizations such as law enforcement agencies. We are glad that – with VeraHunter – hunting for encrypted VeraCrypt containers is just one click away.
Using VeraHunter, you can – of course – refine some parameters and adjust your “hunt” to your individual needs. Most of the time though, just pressing “START” will be enough, as we tried to optimize the hunt process as much as we can, internally. You will find more about those parameters, the thoughts behind them and internal handling further down below on this page.
Take a look at for example the following animated image to get a quick and first glance of how VeraHunter is working. In short, using VeraHunter works in the following 5 and quickly summed up steps:
- Selecting the drives to be hunted
- Refining hunt parameters (optional)
- Listing a file-wise overview of selected drives
- Gathering headers of targeted files
- Calculating final results based on settings & headers
Within Decrypta Technologies Germany, VeraHunter is just one of our numerous helpful applications supporting the everyday work of justice.
How to use VeraHunter?
We’re excited to take you through each step of VeraHunter, designed to assist law enforcement agencies, cybersecurity experts, and digital investigators in the complex world of digital forensics. Let’s dive in and discover how VeraHunter can empower you in your digital forensic endeavors!
Drive selection
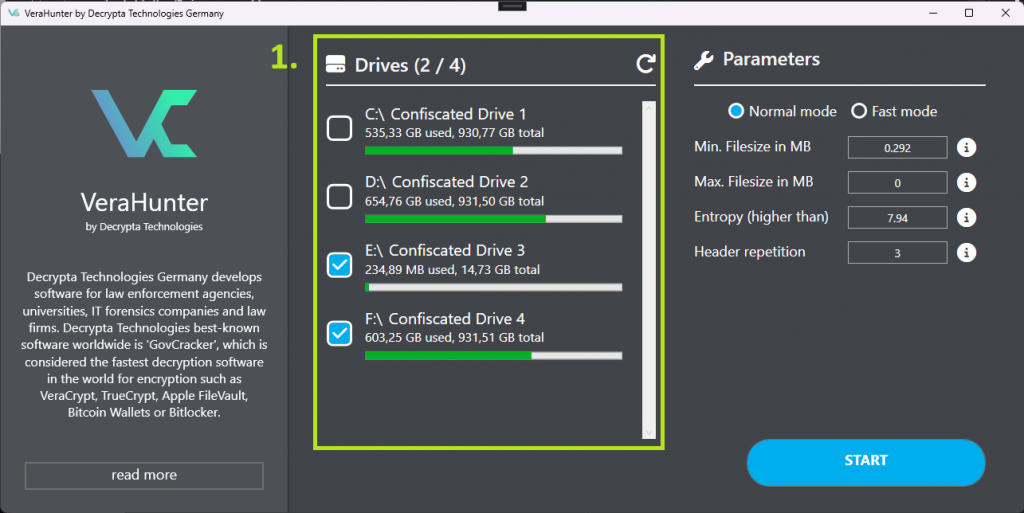
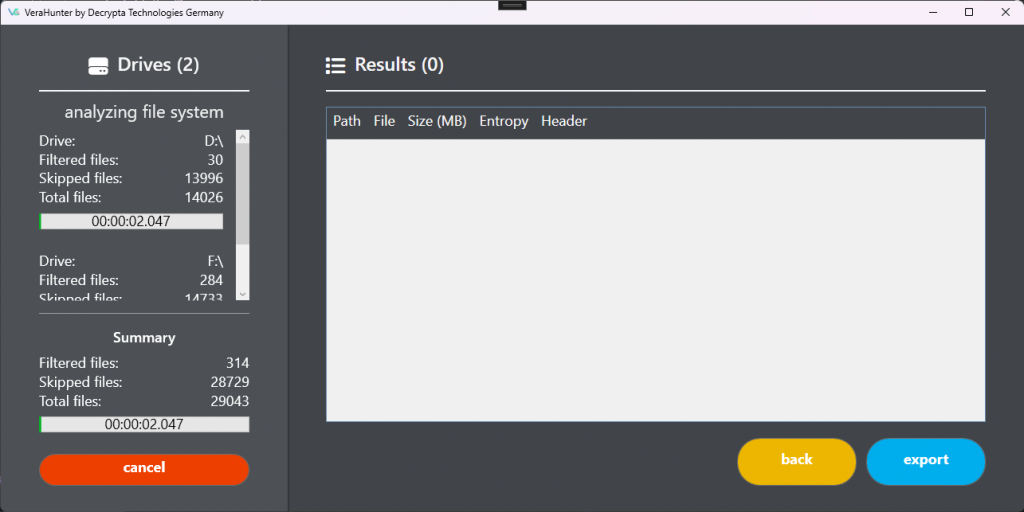
In the first step of VeraHunter, you’re going to see a screen, where you need to choose the devices, that you want to “hunt” (scan) for potential VeraCrypt containers. Please note that the scanning process duration will vary based on the size of the hard drive being analyzed. Larger hard drives may require more time to complete the scan.
You can optimize / speed up the filter process by adjusting the following parameters to your individual needs.
Adjusting hunt parameters
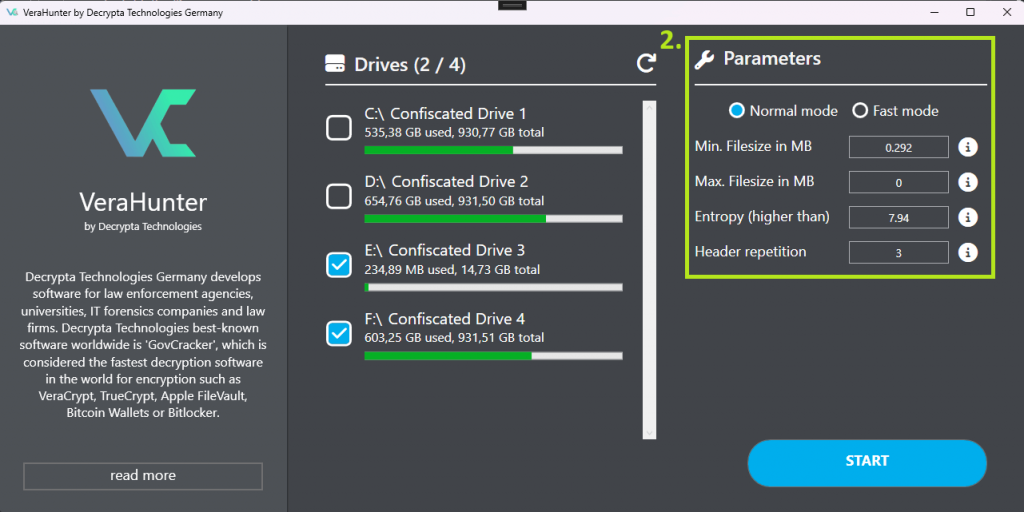
In the next step, we’ll take a look at adjusting the parameters for our VeraHunter tool, fine-tuning the “hunt” to suit your specific needs. Mainly there will be a little switch to speed things up and 4 possible parameters (for now). Of course, we tried to make the default values as good as possible.
Normal or fast mode
Using VeraHunter, there are two modes we generally separate from each other. As the names already suggest, the normal mode will be slower than the fast mode. This results from the internally used process during the analysis.
The key difference while using the normal mode compared to the faster one is, that the normal mode does an additional analysis called “entropy analysis”. This requires a deeper look into each individual file resulting in more work and therefore more time needed. Usually you should probably use the normal mode as the results will be more reliable results – this is why we marked is as default.
Min & max file size
You can use these two parameters to configure, which files will be ignored during the first step. This means, that VeraHunter will ignore files that won’t match this criteria during the initial listing of the system files. Due to our experience in the field of law enforcement and for some nerdy mathematical reasons, we’ve already pre-populated these values for you.
Entropy
This is a nerdy / mathematical thing which involves reading each byte of the file, counting the occurrences of each byte value, and then using that information to compute the entropy of the file’s contents. Shannon entropy measures the uncertainty or randomness in the data, and it’s commonly used in information theory and cryptography.
A file (at least in the normal mode, not in fast mode) will be flagged as “detected”, if it’s entropy matches this criteria. The calculated entropy needs to be bigger than the provided value. We tried to provide you with the best default value of 7.94, so you don’t need to experiment in the first place – allthough you can, of course.
Header repetition
Here you can configure the amount of allowed header repetitions. This means that providing a count of “3” would exclude files having their header occuring more than 3 times. You can read more about this topic in the corresponding section further down below.
Detecting VeraCrypt containers
After following the steps from the last section like selecting the drives to be scanned or configuring the hunt parameters, you can now press the “START” button. This will trigger the actual scanning / detection process of potential VeraCrypt containers. In the next step, we will take a look at the different detection processes VeraHunter will go through.
File system analysis
As VeraHunter is now knowing your drives to be scanned and important others parameters, it can now start doing it’s work. Doing so, it will list every file on each selected drive keeping your filters in mind. Especially the min & max file size filter is important here.
Collection of file headers
Just like humans, recognizing people by their faces being usual, VeraHunter uses an analog approach in this step. Every file that hasn’t been ignored / omitted by the previous filtering process, will now be analyzed. Specifically, VeraHunter is taking something called “a header” from each file and will group those.
This will help VeraHunter to hunt for potential VeraCrypt container files on the selected drives. Taking your configured “header repetition” setting into consideration, it will exclude files having their headers repeat more often than the configured count.
Here’s also the point, where the fast detection mode would end and therefore be faster.
Entropy calculation (normal mode)
If you are using the fast mode, this step would be omitted. Using the normal mode (default), would now start to calculate the entropy for each file. Matching entropies according to your settings would now be added to the results. Only – of course – if no previous configured setting would exclude them in the first place, like the min / max size settings.
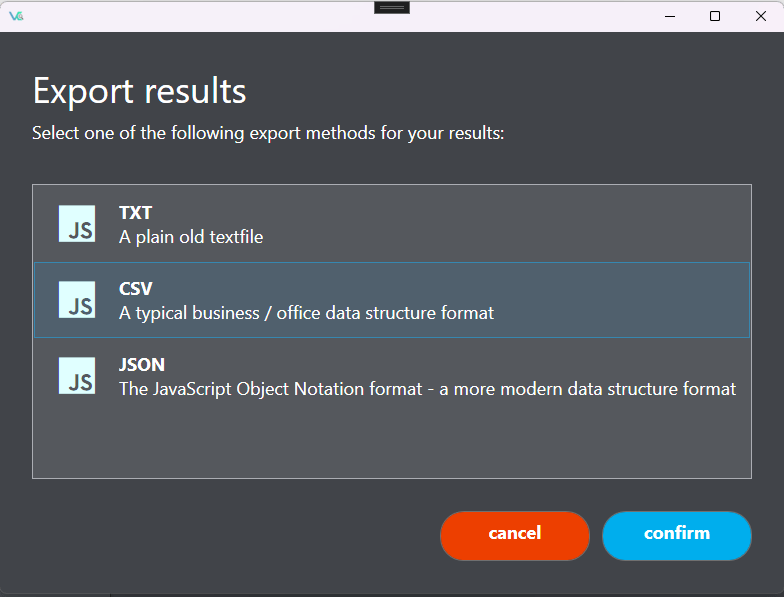
Export of results
Our program offers versatile export options, allowing users to save their results in various formats such as text, CSV, and JSON. This flexibility ensures compatibility with different analysis tools and workflows, making it easier to integrate our program into existing processes or share findings with colleagues.
Freeware
We made the strategic decision to offer our VeraHunter software free of charge to support law enforcement agencies, companies, and other entities involved in criminal investigations. VeraHunter is specifically designed to hunt encrypted VeraCrypt containers, providing a valuable tool for digital forensics and investigative purposes.
By offering this software for free, we aim to democratize access to essential cybersecurity tools, enabling organizations to enhance their capabilities in combating cybercrime effectively. Our commitment to providing VeraHunter at no cost underscores our dedication to promoting digital security and assisting authorities in safeguarding sensitive information and prosecuting criminals.
We believe that by making VeraHunter freely available, we can empower law enforcement agencies, companies, and individuals with the resources they need to address cybersecurity challenges and uphold the integrity of digital investigations.
Screenshots
Get a sneak peek into the world of digital forensics with our free VeraHunter software by taking a closer look at the following screenshots.
Download
VeraHunter is available completely free of charge, reflecting our commitment to supporting the global community in combatting cybercrime and ensuring digital security. Don’t miss out on this invaluable tool – download VeraHunter today and take your digital investigations to the next level.
